Cyber-warfare or blackmail?
An unprecedented cyber attack just took out major banks, government and airport computers in Ukraine
Russian energy firms and Danish shipping company also hit by hackers
Companies across the globe are reporting that they have been struck by a major ransomware cyber-attack.
Ukraine’s national bank, state power company and largest airport are among the targets of a huge cyber attack on government infrastructure. And the list of affected countries, institutions and infrastructure is growing.
Coincidence? Car Bomb, Cyber Attack
The cyber attack – a day before Ukraine marks its Constitution Day – struck hours after a high-ranking intelligence officer was assassinated in a car bombing in Kiev. Police said Colonel Maksim Shapoval, a member of the defense ministry’s main intelligence directorate, was killed in the “terrorist act” on Tuesday.

Ukraine has blamed Russia for repeated cyber attacks targeting crucial infrastructure during the past three years, including one on its power grid that left part of western Ukraine temporarily without electricity in December 2015.
Ransomware

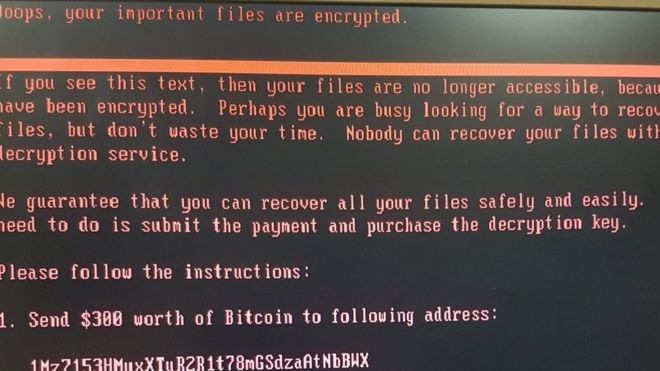
The above image is being displayed by all computers of the Ukraine government. The photo is of a PC displaying a message claiming a disk “contains errors and needs to be prepared”, urging the user not to turn it off.
Images from other affected computers and disabled cash points showed what appeared to be ransomware, demanding a payment of $300 (£235) in Bitcoin to re-gain access to encrypted files.
Analysts said the virus, named Petrwrap or Petya, appeared to work similarly to the WannaCry ransomware that infected more than 230,000 computers in 150 countries last month.
Ukrainian state-run aircraft manufacturer Antonov was among the companies hit, along with power distributor Ukrenergo, which said the attack did not affect power supplies.
The National Bank of Ukraine said an “unknown virus” was to blame, saying several unnamed Ukrainian banks were affected along with financial firms. Oschadbank, one of Ukraine’s largest state-owned lenders, said some of its services had been affected by the “hacking attack” but guaranteed that customer data was safe.
The Boryspil International Airport in Kiev – the largest in Ukraine – were also down. The flight schedule board are not working and the hack caused authorities in the Chernobyl exclusion zone to switch to manual radiation monitoring at the site of the 1986 nuclear disaster.
The Ukrposhta state postal service, television stations and transport were also affected by the attack, which left Kiev metro passengers unable to pay using bank cards. Many ATMs were disabled, displaying the message left by hackers, as were tills in supermarkets.
The cyber attack now affects institutions globally. British advertising agency WPP is among those to say its IT systems have been disrupted as a consequence.
Cyber Attack Spreads Globally
The Russian oil giant Rosneft and a subsidiary, Bashneft, were also hit, as was the British advertising and marketing multinational WPP. Norway’s National Security Authority said an “international company” there was affected, and Martijn Pols, a spokesman for the Port of Rotterdam, said one shipping company, APM Terminals, was targeted.
Dutch-based transport company TNT Express, which was taken over last year by FedEx, also said Tuesday that it is suffering computer disruptions. Spokesman Cyrille Gibot says that “like many other companies and institutions around the world, we are experiencing interference with some of our systems within the TNT network. We are assessing the situation and are implementing remediation steps as quickly as possible and we regret any inconvenience to our customers.” He declined further comment.
The U.S.-based pharmaceutical firm Merck (MRK) also said it’s been hit. Experts suggest the malware is taking advantage of the same weaknesses used by the Wannacry attack last month. A hospital and health care system based in western Pennsylvania says it is dealing with a widespread cyberattack.
Ransomware Source Unknown
“It initially appeared to be a variant of a piece of ransomware that emerged last year,” said computer scientist Prof Alan Woodward.
The Russian cybersecurity firm Kaspersky Lab reported that it believed the malware was a “new ransomware that has not been seen before” despite its resemblance to Petya.
Many firms, including Symantec, have suggested the ransomware is a variant of Petya, a known ransomware. But according to security firm Kaspersky Lab, preliminary findings indicate the attacks are from a new ransomware which it’s calling “NotPetya.”
Researchers say Tuesday’s attacks use a Windows flaw called EternalBlue to spread through corporate networks. WannaCry also leveraged the EternalBlue exploit, which was leaked as part of a trove of hacking tools believed to belong to the NSA. Microsoft (MSFT, Tech30) issued a patch for the exploit in March. Microsoft said it is aware of the reports and is investigating.
As a result, the firm has dubbed it NotPetya. Kaspersky added that it had detected suspected attacks in Poland, Italy, Germany, France and the US in addition to the UK, Russia and Ukraine.
Andrei Barysevich, a spokesman for security firm Recorded Future told the BBC such attacks would not stop because cyber-thieves found them too lucrative.
“A South Korean hosting firm just paid $1m to get their data back and that’s a huge incentive,” he said. “It’s the biggest incentive you could offer to a cyber-criminal.”
A bitcoin wallet associated with the outbreak has received several payments since the outbreak began. The wallet currently holds 1.5 bitcoins – equivalent to $3,500.
An email address associated with the blackmail attempt has been blocked by German independent email provider Posteo.
It means that the blackmailers have not been able to access the mailbox.
